Remember the days of Myspace phishing scams? Well, if you were ever on Myspace no doubt you were sent messages by your oh-so-holy-church-going-friends to look at a porn site, purchase viagra, or just talk to this chick on a webcam. Why would your friend send you such horrible things? Usually because they wanted a free background for their page and didn’t know the first thing about web security.
Basic Security
You see when you give your username and password to a service then they can login to your account. Sounds pretty basic right? But think about it. If they can login to your account they can post anything, change your photos, or whatever else. On Twitter they could even change your password and your email address so that you are locked out of your account without a recovery method.
I would never do something so foolish!
Of course you all have enough sense to not give out your password to just anyone who asks for it. Right?
Wrong. When I looked through my Twitter feed and see little ribbons next to people’s avatars I must point out that they just handed over access to their account to a complete stranger.
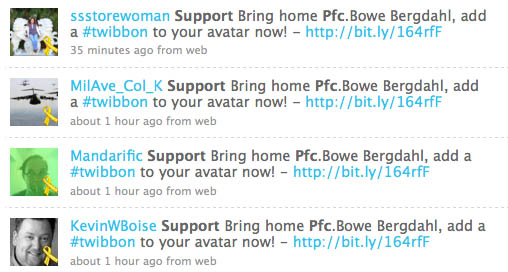
The service Twibbon asks for your username and password which thousands of people are giving up without thinking twice. But it’s okay because they clearly state: “Your login details will not be stored and are only used to update your profile image.” Awesome. They sound nice. Why should you trust them?
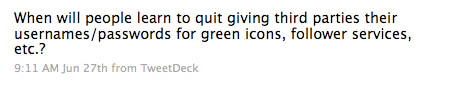
They don’t even look trustworthy! A single line of text shouldn’t make you think otherwise.
It gets worse.
You use email right? Is your Twitter password different than your email password? Yeah, I didn’t think so (to the smart ones who answered yes, congratulations! You passed web security 101). Interested in what you can steal if you know someone’s main email address and password?
- All social media accounts
- Bank Accounts
- Domain Names (It happened to David Airey)
- Blogs
- Your entire online identity
- Online Cell Phone Account
You get the idea. On the web your email address and password are the keys to your virtual kingdom. Why give up something so important just to turn your avatar green?
The best part.
Not only do users give up their password, but they also then post a tweet to tell their friends to do the same. Viral phishing! Now that’s clever.
Web developers should know better!
I found this unfortunate example the other day. The worst part is that many web apps are doing the same thing.
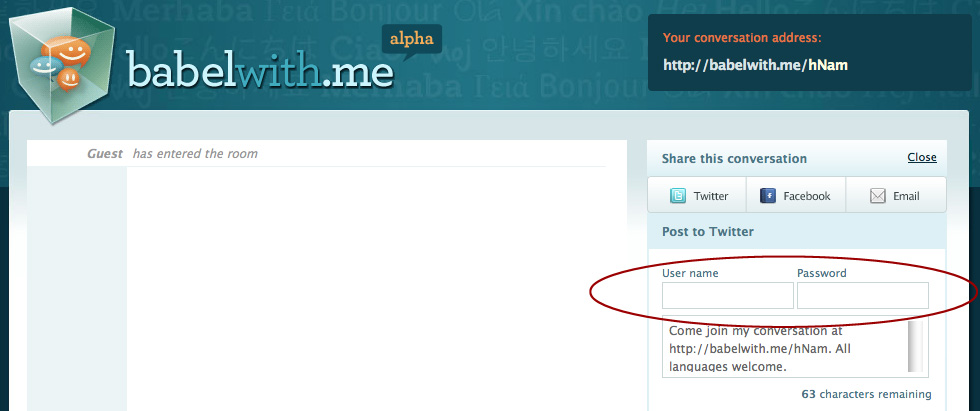
When otherwise intelligent web professionals build services that circumvent basic security principals we are teaching users that it is okay to give up valuable information to an unverified third party service. As designer and developers we need to be setting the standards (and following them!) for security if we are going to fight the increase in online identity theft. Not contribute to it!
There is a better way.
Twitter uses an authentication tool called OAUTH that allows for an app to temporarily access your account, but without requiring you to ever disclose personal information. It also controls what the app can do when they have access. Most of you have seen this screen:

Basically this lets the app do the cool things it was designed to do, but it leaves you completely secure at the same time. It’s just better for everyone.
Think about this.
Your Twitter account is important. Business or personal it is still your brand online. You can’t afford to have it tarnished by a simple, foolish mistake. It would be really embarrassing to post to tell your 2000 followers they should all visit a porn site. It happened on MySpace and it is only a matter of time before it happens on Twitter.
Note: If I called you out specifically or offended you in some way please know that it is only because I am pushing for a safer web (and you were a perfect example!).
Update: This article from CodingHorror.com has some great information (Thanks @davidlwheeler):
You’re Probably Storing Passwords Incorrectly
Follow me on Twitter @nathanbarry
Good post. Interested that you require our email addresses and state that they will never be shared. Can we trust you?
Also, helpiranelection.com – the green avatars – did use OAUTH. And you could immediately remove the authorisation after changing colour.
I just read your post. Awesome write up.
I still find it amazing just how easily sucked in people are when it comes to online security. Do people still lack common sense when it comes to providing information online.
It’s not just social networking sites trawling for data either, I recently looked at a plugin for WordPress, which wanted my email address to activate it. Me being the sceptical me, I thought “why do you want that?” turns out the plugin in question is developed by spammers harvesting email addresses.
It’s the same with email phishing scams with banks. I don’t know how many times I’ve seen TV adverts stating a certain bank will not ask for access numbers but then not even a week later I hear people have fallen victim to the same scams.
Does the Human race not learn or is everyone just living in their own little world thinking “It’ll never happen to me”
@Anon Yes, the Iran Election site does use OAUTH, though I thought when they first started out they only had the option to login with your Twitter credentials. I may be wrong though (it has happened before).
And sharing your email address to post a comment is a bit different then sharing passwords. But I get your point.
@Kimberly I haven’t seen it before with WordPress plugins, but that does make sense. Maybe I’ll write more later on WordPress security.
I liked this author’s philosophy for fixing your insecure passwords. http://www.slate.com/id/2223478/